Mantis Elite – Custom USB-C PD LED Controller / Dimmer
I built this LED controller out of necessity to power a Mantis Elite, that I grabbed off of eBay. My Mantis sadly did not come with an arm or power adapter. I however already had a double boom stand from Old School Industries (http://www.osi-incorp.com/) and they kindly manufactured me an adapter (OSSP30MM) to mount a Mantis Elite onto their stand. I also had parts laying around to easily make a USB-C LED Dimmer for the Mantis. This is actually a superior setup because then the scope can be swung around instead of it being stationary. This also removes the need for even more power bricks due to the USB-C PD connection.
Parts:
(I am putting Amazon links, but these parts can be purchased at 6x less from Ali Express if you do not mind waiting for shipping from China.)
- 9v USB-C PD Trigger
9v “Type-C USB-C PD DC Fixed Voltage Power Trigger Module PDC004-PD PD Decoy Module IP2721 5A Type-C Female Input for Notebook”
https://www.amazon.com/Coliao-Voltage-Trigger-PDC004-PD-Notebook/dp/B09P8HL1CH/ - Mini PWM Controller
“DC Mini Motor PWM Speed Controller Small LED Dimmer 5A 90W 3V 6V 12V 24V 35V Speed Control Switch”
https://www.amazon.com/BOJACK-Controller-Dimmer-Control-Switch/dp/B09P6CMRC9/ - USB-C Extension Cable
“USB 3.1 Type C Extension Cable, USB C Extension Cable Short, USB C Panel Mount 10Gbps 60W USB C Extender Cable for Data & Sync (Straight USB C Male to Female), 1ft/30cm”
https://www.amazon.com/Poyiccot-Extension-Female-Extender-Straight/dp/B086YBP5VW/ - ABS 83x58x34mm Project Box
“Heyiarbeit 1Pcs 83x58x34mm/3.27″ x 2.28″ x 1.34″ ABS White Dustproof With Ear Electronic Junction Box Switch Shell Enclosure Project Box Case DIY Box Junction Case Enclosure”
https://www.amazon.com/Heyiarbeit-83x58x34mm-Dustproof-Electronic-Enclosure/dp/B08XMP19CC - 5.5×2.5mm Barrel Plug Cable
“14AWG DC Power Pigtails Cable,5.5mm x 2.5mm Male Plug Jack to Bare Wire Open End Power Supply Replacement Repair Cord, for Strip Lihgt,CCTV,Monitors,etc-3.3ft/1m “
https://www.amazon.com/LUVMOXE-Pigtails-Replacement-Monitors-etc-3-3ft/dp/B0BKFFRWT1 - Misc: some 14awg wire, a drill / drill-bit set and a knob.
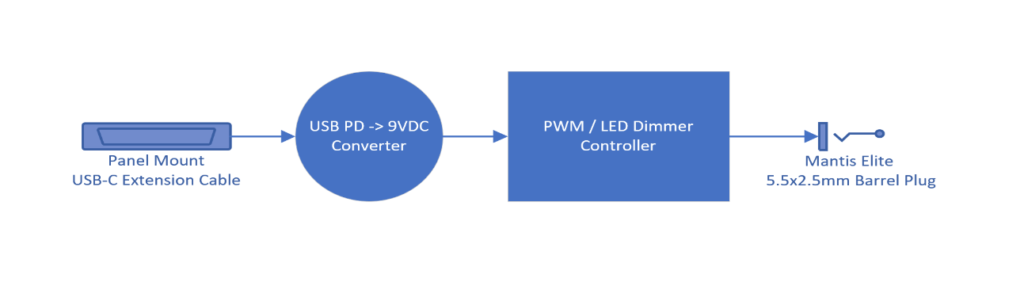
Block Diagram
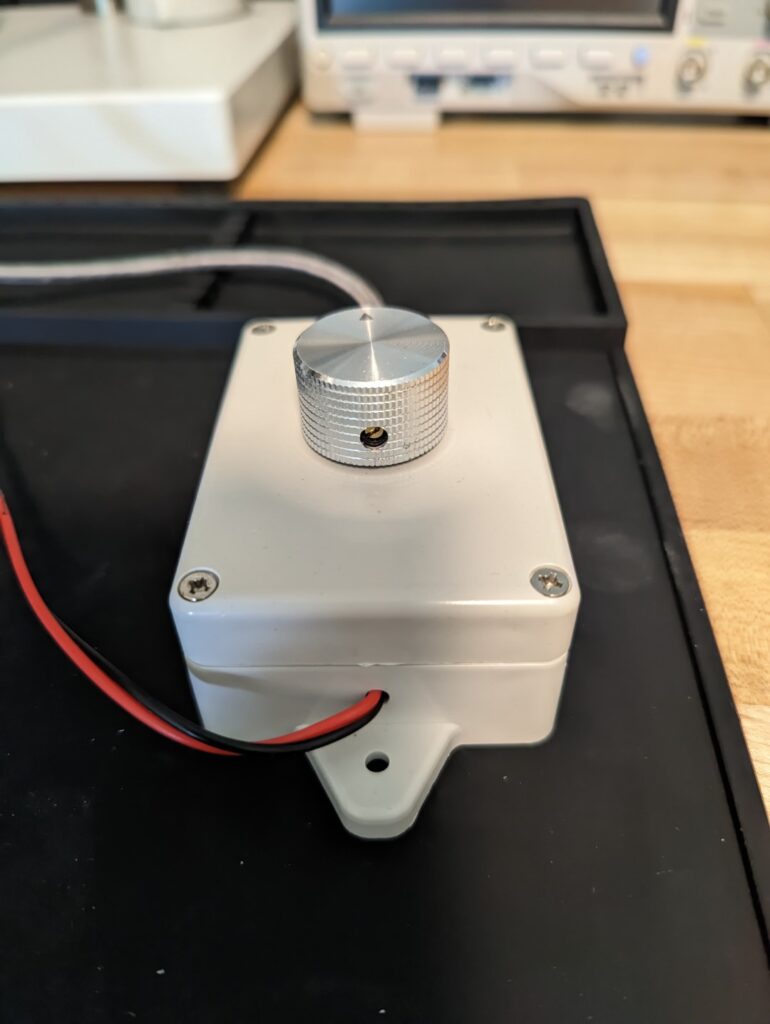
Pics










Reply